各系统身份数据分散
安全与效率受创
拥有统一的身份目录前,
企业管理员需在各系统应用中单独维护多个员工身份与组织架构数据。
若有任何信息变动,都需要进行手动更新,
不仅管理效率低下,
还可能导致信息不一致性和流程延迟的风险。
此外,这种分散的管理方式,
使得企业难以实施一致的安全策略和访问控制。

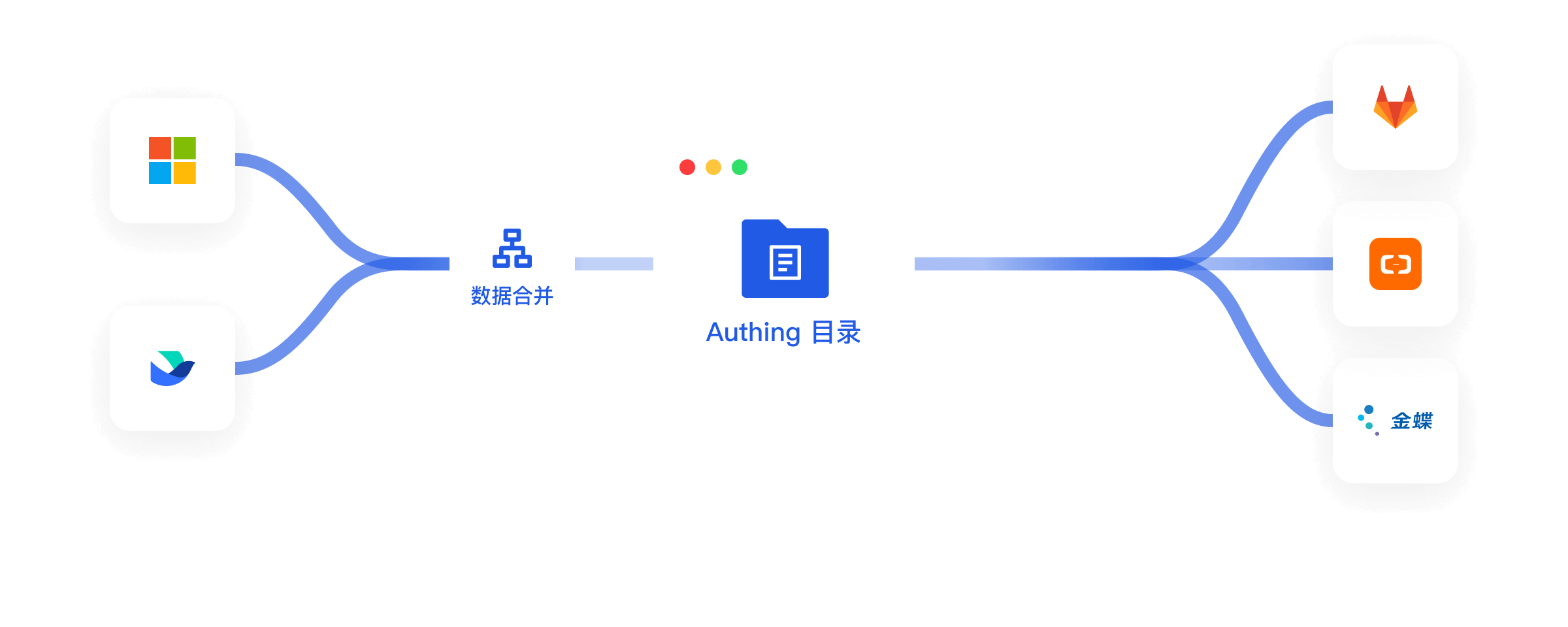
自动同步身份数据
实现统一目录,无需手动维护
通过 Authing 身份自动化能力,企业可选择以企业微信、飞书、钉钉、北森、AD 等应用为统一的上游身份源,将身份数据供给至 Zabbix、销售易、Google Workspace 等下游应用,保持组织架构的一致,减轻 IT 人员的运维负担,减少企业人力成本。
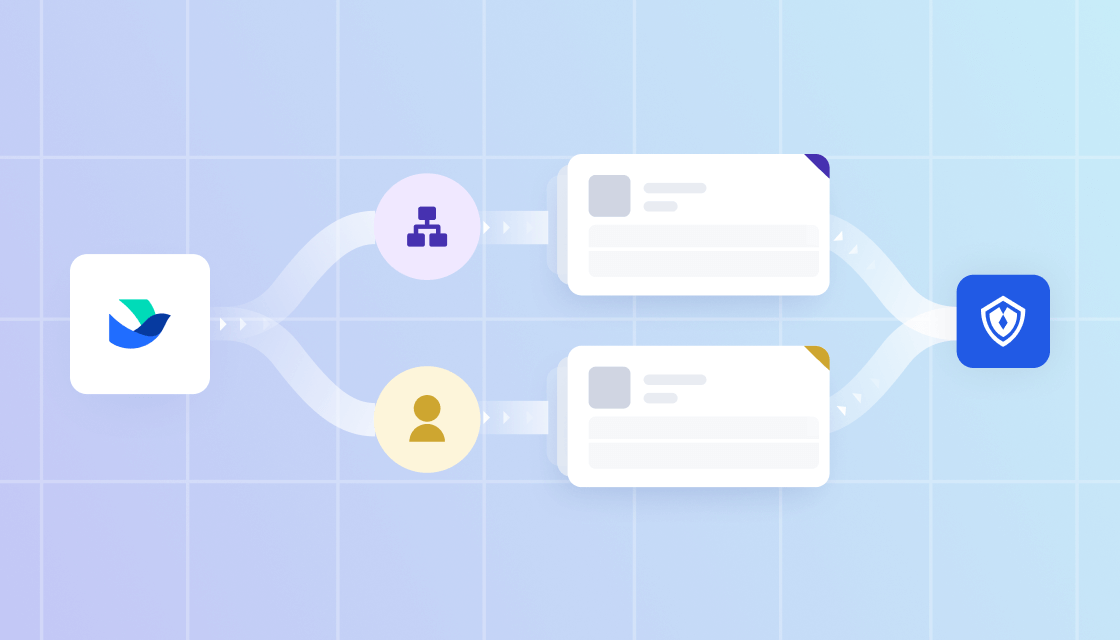
兼顾灵活性和安全性
减少成本的重复投入
集成便捷,依照业务需求灵活拓展、升级迭代
Authing 提供丰富的身份 API/SDK,预集成了 2000+ 海内外应用,每当企业采用新的业务系统,需要进行身份目录的统一时,无需投入繁琐的开发工作,即可快速拓展。

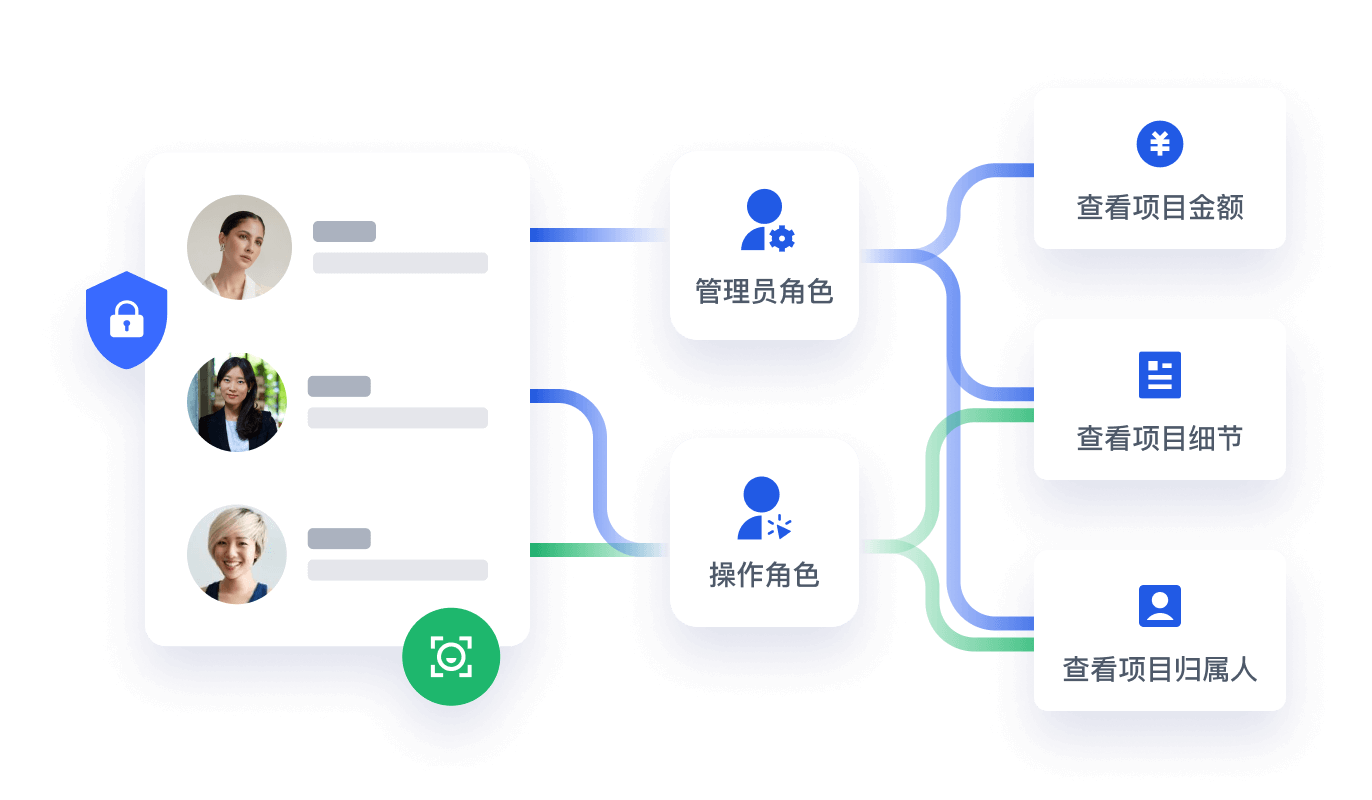
安全可靠,保护企业精密的数据资产
在统一身份目录的基础上,企业可以通过 Authing 的权限管理能力设置授权策略、实现多因素认证,加强用户访问的管控。此外,Authing 采用高强度的加密传输策略,并使用 KMS 管理密钥服务,定期轮换密钥,保护企业敏感数据。